An attacker can create fake DNS entries for the server which may contain malicious content with the same name. Notify me of new posts via email. The program is pre-installed on Kali Linux. Although this is highly unrealistic, it is still a possibility. Now see the highlighted line in the above screenshot. Unified Sniffing was started on the eth0 interface and a scan was run to search for hosts. 
| Uploader: | Maugami |
| Date Added: | 11 November 2014 |
| File Size: | 69.13 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 73043 |
| Price: | Free* [*Free Regsitration Required] |
Now scroll down until you find the heading that says Linux and under that remove both the signs below where it says "if you use iptables". Previous Page Print Page.

No, not that I'm aware of, you can't really force someone to connect to your LAN. You can do it the lame way through launchpad or the cool way using Terminal. Next a web server is setup using Apache2 web server and the fake website is placed within index. Leave a Reply Cancel reply Enter your comment here The attacking machine must have IP forwarding enabled in order to allow traffic to pass through it.
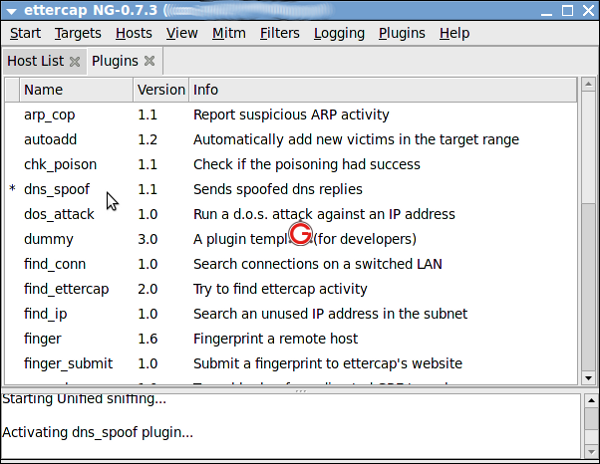
The final thing left to do here is to start the attack. Email required Address never made public.
First open a new console and change to our DNS configuration file located in the following directory: Enough talk, let's do it. An attacker can create fake DNS entries for the server which may contain malicious content with the same name. Use a hardware-switched network for the most sensitive portions of your network in an effort to isolate traffic to a single segment or collision domain.
DNS Spoofing with Ettercap
I hope you enjoyed today's tutorial and hopefully you learned something from it. Filters can be created to manipulate packets to perform a desired function.
First, however, let me explain what can and should be done with the hosts file. Does someone have any advice that could help me tackle the problem?
Tutorial: DNS Spoofing « Null Byte :: WonderHowTo
That is where we can take control of what the victim sees when they get redirected. Learn how your comment data is processed. Hoping to make this highly unrealistic thing realistic. Another nice feature of Ettercap are its filters.
Ettercap is then iniated by running the command ettercap —G which opens the graphical user interface of the program. The on thing I can think of is making an evil twin if they are within range of wireless.
etyercap
DNS Spoofing with Ettercap – wicksnet
It should only take a few seconds depending plugij the size of your network which I assume isn't very large. This demonstrates the vulnerabilities to data integrity and possible vulnerabilities to data confidentiality that can be result from DNS spoofing attacks. Client Machine IP — This should really alert you that it is really that simple to perform a DNS Spoofing attack with very few resources.
I'm sure both issues have to be related, but I couldn't find any useful info online. It was more a statement, since as far as I've read the SSLstrip by moxie won't work with https, but the sslstrip2 by LeonardoNve would work against https.
The attack redirects network traffic from the target machine to reach the attacking machine which provides a fake website to the target machine.
Fun with Ettercap Article: This site uses Akismet to reduce spam.
I apologise if that caused confusion among people. Once you are sure who your victim is, select their IP address from the host list in Ettercap and choose Add to Target 1. Now every time the victim visits the webpage you indicated in the etter. Your example was irrelevant, you will not be able to spoof facebook.

Комментариев нет:
Отправить комментарий